Refer to the exhibit.
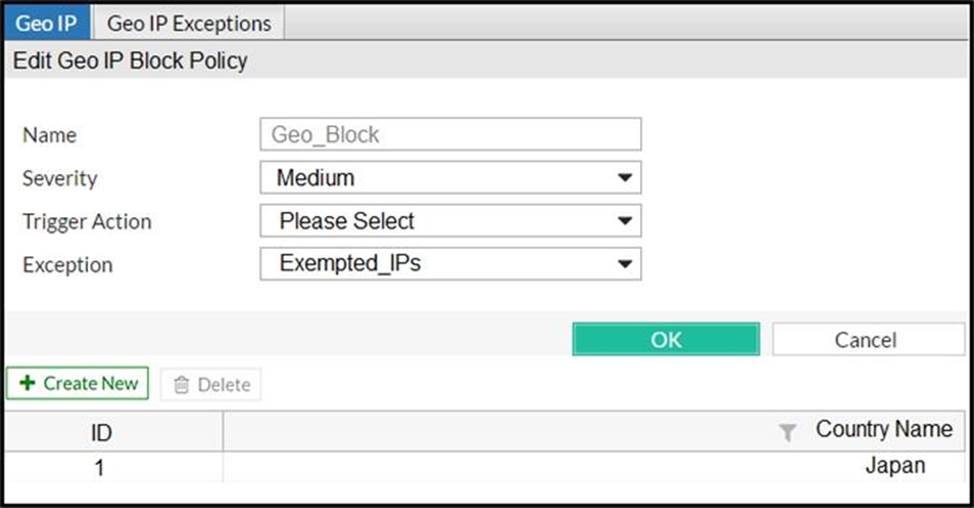
FortiWeb is configured to block traffic from Japan to your web application server. However, in the logs, the administrator is seeing traffic allowed from one particular IP address which is geo-located in Japan.
What can the administrator do to solve this problem? (Choose two.)
A. Manually update the geo-location IP addresses for Japan.
B. If the IP address is configured as a geo reputation exception, remove it.
C. Configure the IP address as a blacklisted IP address.
D. If the IP address is configured as an IP reputation exception, remove it.
Explanation:
IP reputation leverages many techniques for accurate, early, and frequently updated identification of compromised and malicious clients so you can block attackers before they target your servers.
IP blacklisting is a method used to filter out illegitimate or malicious IP addresses from accessing your networks. Blacklists are lists containing ranges of or individual IP addresses that you want to block.
Reference:
https://docs.fortinet.com/document/fortiweb/6.3.5/administration-guide/137271/blacklisting-whitelisting-clients
https://www.imperva.com/learn/application-security/ip-blacklist/